public key infrastructure (PKI)
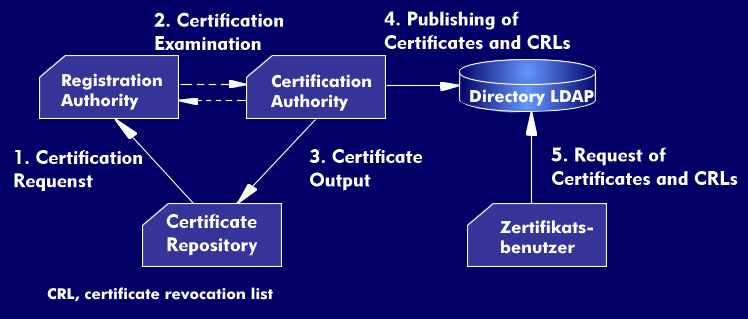
A security infrastructure, a Public Key Infrastructure (PKI), is an environment in which services for encryption and digitalsignature are provided on the basis of public key procedures. In this security structure, the public key of a subscriber(ZN) with the corresponding identification features is authorized by a digital signature from a certification authority( CA).
The security infrastructure instances are responsible for the overall key management. The use of PKI provides a trusted network environment in which communication is protected from unauthorized access by encryption and the authenticity of the communication partner is guaranteed by the digital signature. The various applications of PKI are cryptographically protected. These include the protection of e-mail applications, of desktop systems and of web-based applications, of e-commerce, as well as access controls and secure communication in Virtual Private Networks( VPN). In addition, PKI certification is ideal for providing device or hardware identity to things in the Internet of Things( IoT).
PKI uses two keys with a typical length of 1024 to 2048 bits. A private key, which only the owner and the certification authority know and which is also never read or sent, and a public key, which must be made known to the respective business partner.
The components of the PKI
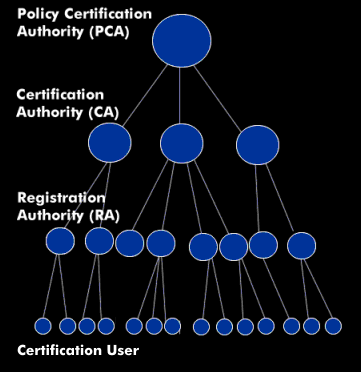
The PKI architecture consists of the instances Policy Certification Authority( PCA), Certification Authority (CA), Registration Authority( RA) and the subscriber, which realize different tasks. In addition, the PKI model includes several functional entities such as the Key Management Center( KMC), the Time Stamping Authority( TSA) and the Key Recovery Center( KRC). The distinguished part of the PKI is called the Trust Center( TC).
A security infrastructure must be transparent to the end user, but the exact processes of key management and certificate management should be hidden from the user. However, he should be able to use the services in a simple way.