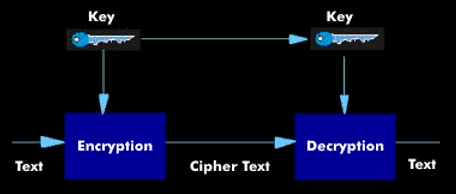
symmetrical encryption
Cryptosystems with symmetric encryption, also known as Secret Key Encryption, know only one secret key, which is used for encryption in the sender and for decryption in the receiver. The sender uses this key to encrypt the message, which the receiver can decrypt using the same key.
In symmetric encryption, only the sender and the receiver have the secret key, which is generated before communication and exchanged between the communication partners over a secure channel. To ensure secure key exchange, only information that cannot be used to draw conclusions about the key may be transmitted. Such a protocol is supported by the Diffie-Hellman algorithm.
Symmetric encryption exists as a block cipher and a stream cipher. The advantage of the symmetric encryption method is that it works very fast. The disadvantage is that unauthorized persons who come into possession of the key can decrypt all messages and also give out encrypted messages themselves.
For the symmetrical encryption procedures with block cipher are used, like the DES algorithm, Kerberos, IDEA, Blowfish and the Rivest Ciphers RC2, RC4 and RC5.